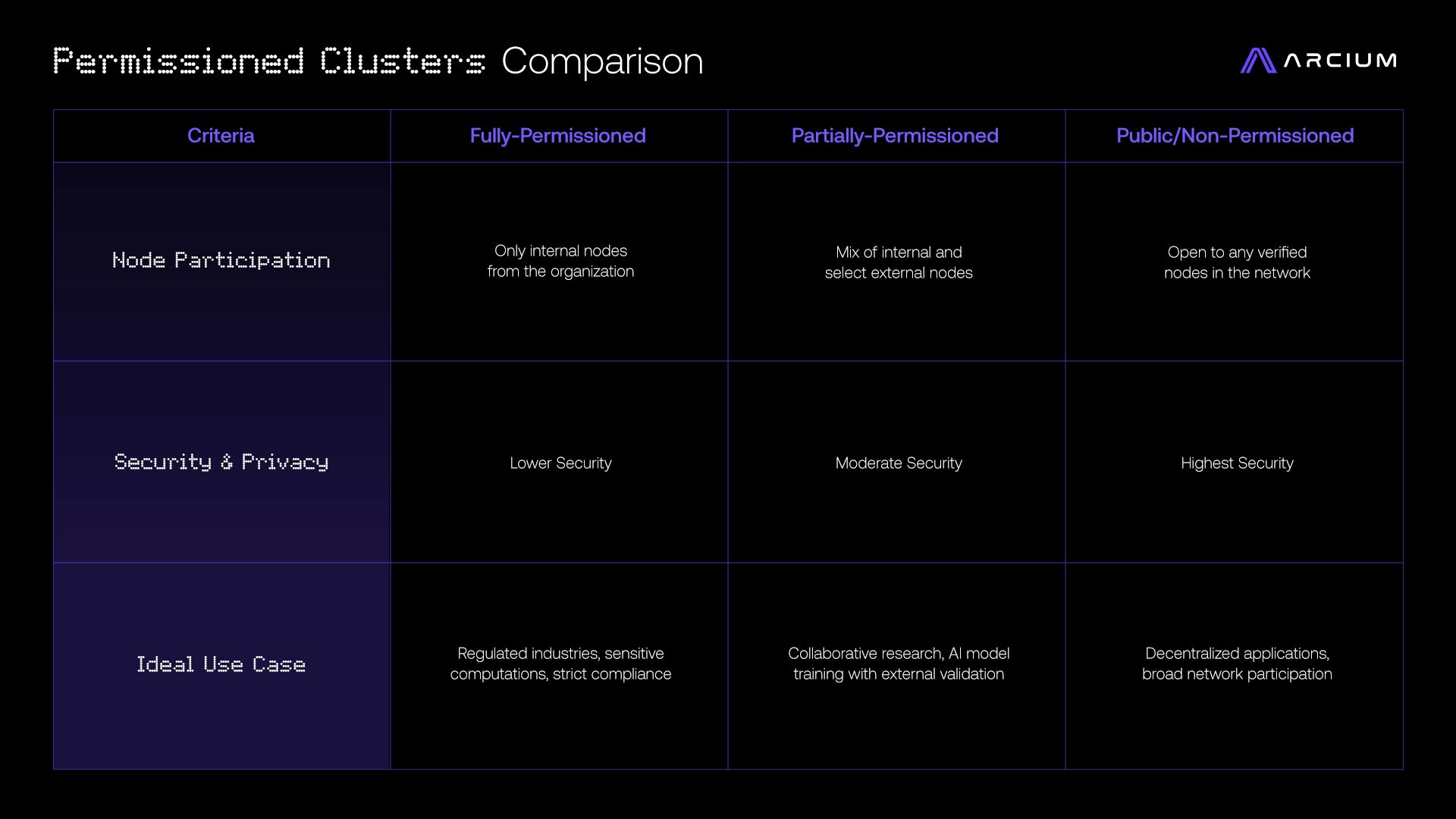
- Fully-Permissioned: Configured for organizations that operate their own infrastructure exclusively, using only their own internal Arx nodes to ensure data privacy and control.
- Partially-Permissioned: A hybrid model that combines an organization’s internal nodes with select external nodes to increase computational power while retaining some oversight.
- Public/Non-Permissioned: Open to all verified nodes in the Arcium Network, providing a decentralized setup ideal for tasks that don’t require strict node control.